Iconico Architecture
This is a simple overview of the Architecture, the different components that can be found in Iconico and how they work together to keep your network running smoothly and promptly notify you when there is an issue.
The Big Picture
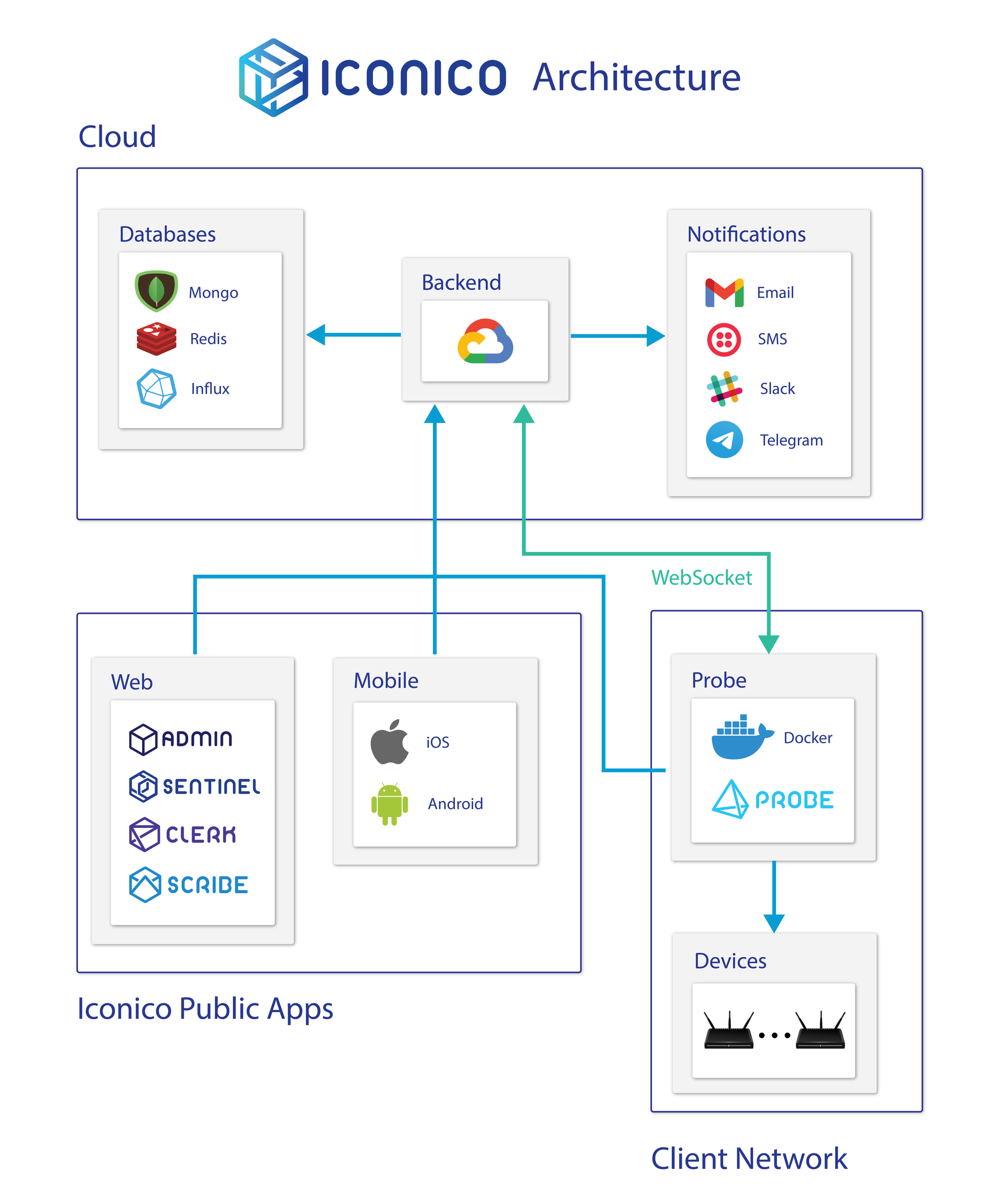
There are three distinct types of Applications running in an Iconico solution:
- Backend: API accessible services connecting to a flexible infrastructure running in Google Cloud. This is the functionality hub of the system. You login against a backend, report stats to it, etc.
- Front-end Applications: Websites or Mobile applications to access your data and device information. This is the application you interact with, both to configure your network, see how it's doing and setup what events you want to be notified about.
- Probe Applications: These run inside of your own private network (which is usually not accessible from the outside internet) and will be performing routine census about your network and its status, it will also report all sensor data (e.g. latency) to the backend so that information is viewable in a front-end application.
How it Works
Backend
The Backend is always on, and will scale up to meet demand. At any given moment, multiple instances might be running across a deployment and on different IP addresses, but conceptually it is best to think of it as a single monolithic application.
Every core functionality of the system can be found there, from authentication services to all notification integrations, including all your subscription management.
Iconico is Payment Processing Compliant (or PCI compliance). All payment methods information is managed directly by Stripe and Iconico won't have access to any of it.
Security
All requests need to be identified by your organization's private API Key and must be performed by a logged in user.
Logged in users must include a secure token that is generated upon login. Tokens have a life cycle of 24 hours so they expire one day after a successful login.
No password is stored in plain text in the system, they are salted and hashed before storage and this hash is then compared to the hash of the password provided for authentication.
Front-end Applications
User facing apps will provide a mechanism for authentication and then interact with the backend to fetch and display information.
Given the flexibility of the backend, any functionality can be built for any platform.
Probes
Probe applications are the gateway into your private network. You can configure your system to run as many probes as you want, each assigned to a subsection of your network.
Even though your private network can be shut off from the internet at large, probe applications are always reachable via WebSockets from our platform. This allows you to execute commands in real time, such as testing whether a particular set of credentials are correct and allow you to access a device.
Probe applications run from docker images, and you can configure docker to assign the resources needed to execute this process.
In Closing
Iconico provides a flexible framework to develop any kind of application for your network, regardless of what you do and the types of devices you use.
We provide three off the shelf, fully developed products:
- Sentinel is a complete network monitoring solution.
- Scribe is a full fledged PPP accounting solution with IP history.
- Clerk allows you to manage device configuration backups.
All these products use flexible pricing so you only pay for what you use.
Contact us at contact@iconico.us or head on over to iconico.us/contact if you want to inquire about building a custom solution that your company needs or simply to ask about the availability of a device brand or feature.
If it doesn't exist already in our system, odds are we want to build support for it.



